Plug-and-Play HIPAA for Healthcare MVPs: The Pluggable Stack That Actually Ships
Here’s the dream: plugging in HIPAA-compliant features to your healthcare MVP and shipping in weeks. Here’s the reality: HIPAA isn’t a checkbox you slap on a widget—it’s an architecture. “Plug-and-play” becomes plug-and-pray the moment PHI touches your stack.
The fastest path isn’t more vendors; it’s a pluggable, healthcare-native foundation where auth inherits across components, audit logs aggregate system-wide, and PHI boundaries hold at every seam.
In this guide, we’ll show you how to filter the slideware, decide what to plug, what to build, and what to wrap (only for non-PHI), and why a modular monolith often beats microservices for MVPs. We’ll close with a pragmatic blueprint—and how Specode assembles compliant pieces without the integration tax.
Key Takeaways
- Start pluggable, not “plug-and-pray.” The fastest MVPs sit on a compliance-first foundation—auth inheritance, unified audit, PHI boundaries, consent cascade—so components actually plug in without retrofits. A HIPAA-ready healthcare AI builder (e.g., Specode) lets you assemble this backbone by chat with instant preview, then tailor only what’s net-new.
- Retrofitting is a curve, not a task. First component = X hours; second ≈ 1.5X; third ≈ 2X as consent, audit, and PHI boundaries multiply across edges. Keep a modular monolith and use the AI builder to auto-wire scopes, logs, and routes—so you’re adding features, not re-plumbing.
- Filter vendors in 5 minutes. Demand a real BAA, auth inheritance, an audit aggregation endpoint, licensing webhooks, and scoped consent. If they tout an AI builder, verify it also provides a Change Log with one-click restore and role-scoped testing—most “HIPAA-ready” plug-ins fail here.
When "Just Use What Everyone Else Uses" Becomes a HIPAA Nightmare

Every developer has that moment: three weeks into a healthcare build, someone asks, “Wait, why aren’t we just using Stripe?” It’s a reasonable, plug-and-play-sounding question—until you discover that Stripe won’t sign a Business Associate Agreement (BAA), the legal document that makes any vendor HIPAA-compliant when handling protected health information. Without it, you’re one patient name in a transaction away from violating federal law.
The stakes couldn’t be higher. HIPAA penalties in 2025 now reach $2,134,831 per violation for willful neglect, with separate violations counted for each patient record exposed. That friendly reminder email with appointment details sent through your “just plug it in” standard Firebase config?
If it contains any patient identifiers and Firebase Messaging isn’t covered under Google’s BAA, each email could theoretically trigger its own violation. A modest patient panel of 1,000 could mathematically expose you to billions in potential penalties—though enforcement typically caps annual penalties per violation type.
The Technical Requirements That Break Standard Tools
The problem runs deeper than missing BAAs. Healthcare demands architectural patterns that consumer tools actively resist:
- Audit logging permanence: Stripe records personal data within transaction data for fraud detection and shares it with third-party payment providers, creating an uncontrolled PHI exposure surface
- Data residency controls: Your Firebase Realtime Database can't guarantee PHI stays within specific geographic boundaries
- Consent cascading: When a patient revokes consent, every downstream system must honor it—impossible when Stripe's fraud partners have already ingested the data
- Breach notification coordination: You have 60 days to notify affected patients of a breach, but good luck tracking PHI that's been shared through Stripe's network of processors
Standard configurations become compliance nightmares. While some Firebase services like Firestore fall under Google Cloud's BAA, critical features like Firebase Authentication, Realtime Database, and Messaging don't.
Teams discover this after building their entire auth flow around Firebase Auth, facing months of rearchitecture or accepting massive compliance risk.
Payment stack caution (Stripe):
“Stripe is not HIPAA compliant and – other than its payment processing services – should not be used by covered entities and business associates to create, collect, store, or transmit Protected Health Information (PHI).” — HIPAA Journal.
The cruel irony? These tools work perfectly for 99% of businesses. But healthcare lives in the 1% where “mostly secure” and “probably compliant” can be company-ending. The moment you treat generic, so-called plug-and-play components as PHI-ready, you end up building a HIPAA wrapper—often costing more than starting with healthcare-native infrastructure.
The Hidden Architecture Tax: What Makes Healthcare Components Actually Pluggable

Most teams discover the hard way that "pluggable" healthcare components are about as pluggable as a European appliance in an American outlet—technically they fit, but nothing actually works the way it should. The real issue isn't the individual components; it's the seven architectural requirements that 90% of solutions completely miss.
Here's what nobody talks about at the vendor demos: true healthcare pluggability requires synchronized orchestration across authentication, audit trails, PHI boundaries, licensing, consent, retention, and breach protocols. Miss any one of these, and your "plug-and-play" dream becomes a compliance nightmare with a side of engineering debt.
Authentication Inheritance: The First Domino
The problem hits immediately: consumer tools assume every service owns its own login. Stripe wants one, your video platform another, your messenger a third. In healthcare that’s not just annoying—it’s broken.
Auth must inherit across the stack. When a provider signs in, that context has to flow through scheduling, messaging, documentation, billing—while enforcing:
- role-based access
- cross-service sessions
- PHI-safe tokens
- federated identity for multi-site orgs
Retrofitting isolated components to behave this way routinely burns hundreds of engineering hours—before you even touch the next constraint.
The Audit Log Black Hole
Ask your vendor how their “HIPAA-compliant” component aggregates audit logs. Watch the scramble. Every PHI-touching service must emit immutable logs—who, what, when, why—but with multiple components you need system-wide, searchable, time-synchronized trails:
- unified schemas
- centralized aggregation with chain-of-custody
- clock sync across services
- queries that follow one patient across modules.
Without it, an incident becomes a scavenger hunt through mismatched formats and silos—and the 60-day clock doesn’t care. Try explaining that to OCR.
PHI Boundaries: Where Components Leak
The scariest failures happen at the seams—where so-called plug-and-play components quietly turn plug-and-leak. Each service needs crystal-clear delineation of where PHI lives, how it moves, and what can cross service boundaries. Most teams discover too late that their video platform is storing recordings with PHI, their scheduling tool is caching patient names in Redis, or their notification service is logging phone numbers.
Proper PHI boundary management requires:
- Explicit data classification at every service interface—what's PHI, what's de-identified, what's metadata. No assumptions.
- Controlled data flow with encryption at every hop, not just at the edges. Your internal service mesh needs the same security as external APIs.
- Segmentation strategies that prevent PHI from accidentally spreading through caches, logs, or temporary storage.
Provider Licensing: The State Line Problem
Nobody thinks about provider licensing until a Texas-licensed physician tries to treat a patient in Oklahoma through your platform. Suddenly, your innocent scheduling component needs to verify licensing across state boundaries—at runtime, for every interaction.
This isn't a simple lookup. You need:
- Real-time license verification against state boards
- Multi-state license tracking for providers with compact privileges
- Specialty certification validation
- License expiration monitoring with automated suspension
Most "healthcare-ready" components punt on this entirely, leaving you to build the verification layer yourself.
The Consent Cascade Nightmare
Consent isn’t a binary toggle you can just plug in—it’s a cascading, scoped set of permissions that must propagate across every component. Patients may allow treatment but not research; primary care but not specialists; medical records but not mental-health notes.
Every so-called pluggable component must check consent before acting: no SMS reminders without opt-in, no analytics for opt-outs, billing ≠ clinical rights. Architectural fix: a centralized consent service gating all PHI ops and enforcing propagation. Otherwise, one misrouted message = violation.
Data Retention Synchronization
Retention rules conflict: HIPAA 6y, CA 7y, insurers 10y; billing ≠ clinical. Multiply across components and you get chaos—some delete too soon, others hoard. Solve with:
- Centralized retention policy engine
- Cascade deletes across dependents
- Legal holds across all components
- Audit trails that outlive purged data
Breach Notification: The Coordination Challenge
When a breach happens—not if, when—you have 60 days to notify affected patients and potentially 24 hours for media notification if it affects 500+ people. But first, you need to know what was breached across all your components.
This requires pre-built coordination protocols: which component detected the breach, what data was exposed across the system, which patients were affected, and who needs notification. Every component needs standardized breach detection and reporting APIs, not just security theater.
The Reality Check
These seven requirements aren't nice-to-haves—they're the minimum viable architecture for truly pluggable healthcare components. Specode's components are designed from day one with these requirements baked in. Each component shares authentication context, aggregates audit logs centrally, respects PHI boundaries, validates licensing, inherits consent, synchronizes retention, and coordinates breach responses.
That's the difference between components that are actually pluggable and ones that just claim to be.
The Real Math: Retrofit vs. Native vs. Build
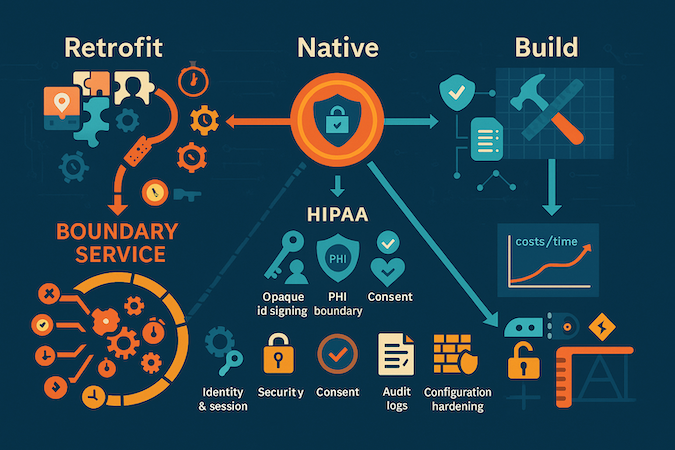
Let’s kill the fantasy: most “plug-ins” work great—until you must keep PHI out of them and still pass an audit. The real bill isn’t the license; it’s the wrapper: isolating flows, scrubbing identifiers, enforcing consent, and proving it with unified logs.
Retrofit Reality
You can keep best-in-class services if they never see PHI. That means a boundary service that maps opaque IDs, signs webhooks, strips metadata, and reconciles events to your clinical system without leaking context. The wrapper is the work.
Where the Hours Go
- Identity & session unification (inherit auth, don’t duplicate)
- PHI boundary enforcement (mappers, redaction, event hygiene)
- Centralized auditing (trace one patient end-to-end)
- Configuration hardening (MFA, network policy, PITR, key rotation)
Integration Debt Compounds
First retrofit ≈ X hours. Second ≈ 1.5X (now you’re managing boundaries between tools). By the third, expect ≈ 2X just to orchestrate consent, audit, and segmentation across services. The surprise isn’t any one tool—it’s the edges between them.
TechCrunch has reported HIPAA lifts often run $50k–$100k in consulting plus ~200 hours of manual work to stand up controls and documentation.
Native vs. Retrofit vs. Net-New
- Retrofit: Fast start; wrapper engineering dominates maintenance.
- Healthcare-native: Slightly slower start than naïve plug-in, but BAAs/audit/PHI boundaries are prewired, so total hours flatten sooner.
- Build: Max control; highest day-1 cost; best long-run if workflows are your moat.
Bottom line: You either pay to make it work safely (wrappers) or pay to own it natively (healthcare-first stack). The only losing move is pretending “plug-and-play” applies to PHI.
Speed Without Shortcuts: The Plug-In Strategy That Actually Works
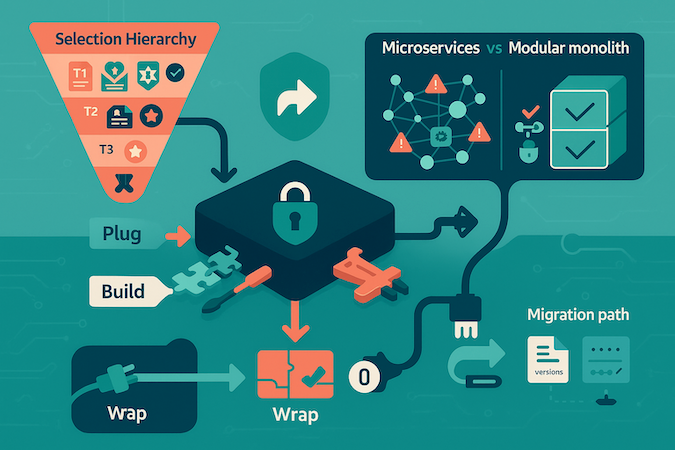
Healthcare isn’t allergic to speed—it’s allergic to retrofitting. Shipping in weeks (not quarters) comes from starting with the right foundation and being ruthless about what you plug, build, or wrap—not from cutting corners.
Counterintuitive truth: the fastest path starts with healthcare-native infrastructure. Not badgeware. Not duct-taped wrappers. Components must share auth context, aggregate audit logs, and respect PHI boundaries by design. (Your prior sections establish why this matters; this is the execution plan.)
The Selection Hierarchy (read-first filter)
- Tier 1 – Compliance architecture: BAA coverage, auth inheritance, unified audit, consent cascade.
- Tier 2 – Healthcare specifics: licensing checks, state rules, field-level PHI encryption, breach hooks.
- Tier 3 – Features: only after T1–T2 pass.
(Details live in the 5-minute test + doc red flags you already wrote.)
The Plug / Build / Wrap Framework
- Plug when the component is healthcare-native and compliance is verifiable without altering core behavior (e.g., telehealth SDKs, healthcare scheduling, DICOM viewers).
- Build when it’s your differentiation, no compliant fit exists, or a wrapper would exceed the feature’s scope.
- Wrap only for non-PHI use of non-healthcare services, with a true air gap (opaque IDs, metadata scrubbing). If wrapper effort > ~one sprint, re-evaluate.
Why Microservices Slow MVPs in Healthcare
Each service boundary adds auth propagation, consent checks, PHI enforcement, unified audit, and separate BAAs/security reviews. Complexity is multiplicative. For MVPs, a modular monolith with healthcare-native components beats five tidy services that can’t share a compliant auth context.
The Migration Path
Pick components with export APIs; document every PHI touchpoint; isolate integration code in dedicated modules; add abstraction only where migration is likely; version audit logs so compliance survives transitions. This is how you ship fast now and avoid an 18-month rewrite later.
The Component Evaluation Framework Smart Teams Use

Three weeks into vendor selection, you’re drowning in “HIPAA-compliant” and plug-and-play promises. Every platform swears it’s healthcare-ready, but when you ask for a BAA that covers your actual data flows, half ghost you and the rest send carve-outs that exclude exactly what you need. Here’s the evaluation framework that cuts through pluggable vendor theater in minutes, not months.
The brutal reality: most “healthcare-ready” plug-ins fail basic architectural tests before you even touch compliance. Smart teams run a structured evaluation that exposes deal-breakers before anything gets plugged in—saving weeks of integration attempts that were doomed from the start.
The 5-Minute Litmus Test That Eliminates 80% of Vendors
Before demos, before pricing calls, before technical deep-dives, run this quick filter:
Question 1: "Show me your signed BAA template right now." If they need legal review, can't produce one immediately, or their template excludes "transactional data" or limits coverage to "customer account information" instead of explicitly covering PHI—you're done. Microsoft's BAA includes clauses excusing them from patient access requests because PHI isn't stored in designated record sets, while AWS makes compliance conditional on correct customer configuration. Know what you're signing.
Question 2: "How does your component inherit authentication from our existing auth provider?" Listen for OAuth2, SAML, JWT propagation. If they start explaining their own login system, that's a wrapper you'll be building. Dead-end for healthcare where single sign-on isn't optional—it's table stakes.
Question 3: "Where's your audit log aggregation endpoint?" No unified audit API = you're building log scrapers. Healthcare requires immutable, searchable trails across all components. If they offer CSV exports or per-component dashboards instead of programmatic access, move on.
Question 4: "What happens when Wyoming revokes a Texas provider's reciprocity privileges?" Blank stares mean they've never dealt with multi-state licensing. Real-time license verification requires checking 56 U.S. jurisdictions and tracking status changes across 800+ provider taxonomies. If their answer doesn't include webhooks for license status changes, you'll be polling manually.
Question 5: "Show me patient consent cascade in your API." If consent is binary (on/off) instead of scoped (treatment yes, research no, behavioral health limited), you'll need architectural surgery later. Look for granular permission models, not all-or-nothing flags.
Documentation Red Flags That Signal Integration Hell
The docs tell the truth marketing won't. Here's what sends experienced teams running:
- No API reference for audit retrieval—just UI screenshots of reports
- Authentication examples showing API keys in headers instead of delegated OAuth tokens
- Data models with "user" objects instead of "patient/provider" separation
- Webhooks without HMAC signatures or timestamp validation
- Rate limits under 100 requests/second for synchronous APIs (license checks can't queue)
- No mention of clock synchronization for distributed systems
- "Contact us for enterprise features" where enterprise means HIPAA
The worst sign: documentation that explains their internal architecture instead of your integration pattern—if they can’t show a pluggable API surface, you’re in for months of undocumented edge cases.
The BAA Fine Print That Actually Matters
BAAs must establish permitted uses of PHI, require appropriate safeguards, mandate breach reporting, and ensure proper disclosure handling—but the devil's in what vendors exclude.
Watch for these poison pills:
"Customer Data" vs. PHI Coverage: Many BAAs cover "customer data" or "account information" but explicitly exclude PHI from certain services.
The Configuration Escape Clause: Vendors love adding "when properly configured" language. If their BAA makes compliance conditional on settings you control, one misconfigured flag voids your protection.
Subprocessor Carte Blanche: Some BAAs let vendors add subprocessors with 30-day notice—or less. Every subprocessor multiplies your attack surface. Demand approval rights or at least veto power.
Breach Notification Delays: HIPAA gives you 60 days; some vendor BAAs give themselves 30 to notify you, leaving you just 30 to investigate and report. Non-starter.
The Bottom Line
This framework filters out platforms that waste months of integration effort. Apply the filter before anything gets plugged in. It saves months, forces reality over rhetoric, and exposes who’s done the architecture vs. who expects you to.
What's Coming: AI-Powered Healthcare Assembly

Forget the drag-and-drop promise that still requires 200 hours of configuration. The real shift happening right now? AI that understands healthcare's compliance maze from day one and assembles production-ready systems in hours, not months.
The AI healthcare market is exploding from $26.57 billion in 2024 to $187.69 billion by 2030, but here's what most of that growth misses: general-purpose AI tools still fail catastrophically in healthcare.
ChatGPT won't sign BAAs. Claude's consumer version can't touch PHI. When hospitals add patient data to AI chat tools for documentation or patient communication, the AI developer becomes a business associate under HIPAA and must comply with all its requirements—which most don't.
The Intelligence Layer That Actually Gets Healthcare
The game-changer isn’t just AI—it’s healthcare-trained, pluggable AI orchestration that knows:
- PHI boundaries aren't suggestions, they're federal law
- Audit trails must aggregate across plug points, not live in silos.
- State licensing checks run at component boundaries every time.
- Consent cascades through everything you plug in.
By 2024, over 65% of application development will use low-code tools, but healthcare's getting something better: AI builders that don't just generate code—they generate compliant, integrated systems.
Tools like Blaze's drag-and-drop interface with built-in HIPAA compliance right out of the box and AI-enabled visual creators that build apps using ChatGPT with pre-built integrations are proving the model works.
From Configuration Hell to Conversational Assembly
Traditional "no-code" still meant weeks of:
- Manually mapping data flows between components
- Configuring authentication inheritance across services
- Setting up consent management for each integration
- Testing PHI boundary enforcement at every handoff
The new paradigm? Tell the AI your requirements in plain English. It assembles pre-verified, HIPAA-ready components that already share authentication, consent management, and audit infrastructure. AI's predictive analytics identify patterns for proactive care while handling complex tasks like data security and real-time synchronization. No more integration debt. No more compliance gaps between services.
Why Healthcare-Specific Training Changes Everything
Generic AI builders treat healthcare like any other vertical—add some encryption, call it HIPAA-ready and pluggable. Healthcare-trained systems understand that:
- Provider workflows aren't linear; they're interrupt-driven
- Documentation isn't data entry; it's legal record
- Integration isn't API connection; it's BAA coverage, PHI boundaries, and state-by-state licensing
The platforms winning now—tools using government-grade security on AWS GovCloud, builders with pre-negotiated pharmacy integrations, systems that handle 42 CFR Part 2 consent automatically—weren't accidents. They were built by teams who've eaten the compliance glass so you don't have to.
The reality check: We're 8-12 months from AI builders that turn a requirements doc into a running, compliant healthcare system in under a couple of weeks. Not a demo. Not a prototype. Production-ready, with every component pre-integrated, every BAA in place, every audit trail connected. That's not the future—teams are already piloting these systems today.
How Specode Solves the Pluggability Problem

Most platforms force a false choice: accept pre-built rigidity or burn months wiring tools that were never meant to talk. Specode took a different path—every component shares the same auth layer, audit spine, and consent model from day one. No adapters, no “integration phase,” no doubled timelines.
What Changes with Specode
- Shared context by design: Auth inheritance, role scopes, and session propagation across components.
- Unified evidence trail: Centralized, immutable audit logs you can query end-to-end.
- Automatic consent cascade: Permissions extend when you add components (no re-plumbing).
- Hard PHI boundaries: BAAs, field-level controls, and event hygiene built in—not bolted on.
The AlgoRX rollout illustrates the economics: eligibility, provider workflows, ePharma routing, and real-time, multi-pharmacy checkout assembled from pre-integrated components in weeks: reported $1M sales by month two and 12× ROI by avoiding the integration tax.
What You Stop Doing
- Rebuilding wrappers for every vendor.
- Chasing consent bugs across services.
- Reconciling twelve log formats during audits.
- Freezing roadmaps for “compliance hardening.
Under the hood, components are born HIPAA-ready—PHI boundaries, BAAs, audit trails, breach hooks—so when you add, say, symptom tracking to telehealth, governance extends automatically instead of triggering another security review.
AI Assistant: Build by Chat, See It Live
Describe the workflow you want and watch it assemble on the shared auth/audit/consent fabric—with an instant preview. Because components already speak the same language, the healthcare AI BUILDER extends flows without the usual “integration phase.”
Start on a healthcare foundation (roles, consent, audit), then flip on only what matters—payments, telehealth, eRx, wearables, EHR/EMR—and connect your own data early so screens reflect real entities, not mockups. When something’s truly unique, drop into code or tap our Custom tier for hands-on help or purpose-built AI agents. No AI magic—sequence and ruthless focus.
- Prompt → preview across components (intake, scheduling, messaging, checkout).
- Integration switchboard: EHR/EMR, labs, pharmacy, insurance, custom APIs.
- Guardrails: Change Log restore and role-scoped testing for safe iteration.
- Full code ownership: export anytime; no lock-in.
- Your team or ours: combine AI-assisted assembly with custom development.
Try it free—open a Specode workspace, ask the AI builder for “auth + consent + unified audit,” drop in scheduling, preview, then connect a sandbox EHR. Pluggable, not plug-and-pray.
Frequently asked questions
It means components share auth, consent, audit, and PHI boundaries by design, so you can add or swap modules without wrapping each one in custom compliance code.
Yes, if they never see PHI. Put them behind a boundary service that maps opaque IDs, strips metadata, signs webhooks, and reconciles events without leaking clinical context.
Every service boundary adds auth propagation, consent checks, PHI enforcement, unified audit, and often a separate BAA. That’s multiplicative work you don’t need on day one.
Ask for a signed BAA template, show-me auth inheritance (OAuth2/SAML/JWT), a unified audit-log API, license-status webhooks, and scoped consent. If any are missing, stop there.
It’s the custom layer you build to keep PHI out of non-BAA tools while preserving workflows. As you add components, wrapper hours climb because edges—consent, audit, identity—multiply.
Specode’s components arrive with shared auth context, centralized audit, consent cascade, and PHI boundaries baked in, so you assemble features instead of re-plumbing compliance.
Use it to describe requirements and assemble pre-verified, HIPAA-ready components that already share auth, consent, and audit—accelerating delivery without creating integration debt.









