The Trap of No-Code in Healthcare: Why You Need Full Code Ownership
No-code in healthcare doesn’t fail because it’s flimsy. It fails because it’s seductive. You ship a working workflow before the first “build vs buy” meeting ends. The clinic lead is happy. The demo looks real. Everyone feels like they’re finally outrunning the backlog.
And for a while, you are.
The trap snaps shut the moment your app stops being a prototype and starts being a product:
- when PHI becomes non-negotiable,
- when an EHR integration stops being a “Phase 2” slide,
- when an audit asks “show me” instead of “tell me,”
- when a bug becomes an incident with a clock attached.
Suddenly, “we can change it in the builder” isn’t speed — it’s fragility, because the most important parts of your system live somewhere you don’t truly control.
To be clear: no-code has a rightful place in healthcare. It’s a fantastic way to discover workflows, validate demand, and align stakeholders. But if you’re building something that must survive compliance scrutiny, integration complexity, and real operational risk, you need a different definition of “fast.”
In healthcare, velocity without ownership is just deferred rebuilding — with interest.
Key Takeaways
- In healthcare, “compliance” is operational proof—if you can’t show auditability, you don’t control PHI.
- No/low-code can accelerate workflows, but the real risk is ownership gaps: data control, permissions, integrations, and migration.
- “We can export” is not always an exit plan—without structure, lineage, and system-of-record boundaries, your rewrite is just delayed.
What No-Code Actually Gets Right
By 2025, Gartner expects 70% of new applications built by organizations to use low-code/no-code (up from <25% in 2020). That doesn’t happen because everyone suddenly lost their minds — it happens because no-code is insanely good at compressing the “figuring it out” phase.
In healthcare, it gets the whole room aligned faster than any PRD ever will. Instead of debating requirements, you watch a workflow run. You see where intake breaks, where approvals stack up, where the “simple” step is actually three roles, two exceptions, and a PDF someone still prints (of course).
It’s also the fastest path to stakeholder buy-in: clinicians and ops teams can touch the thing early, and you can iterate without waiting for a sprint ceremony to bless your next button.
Used correctly, no-code is a truth machine: rapid validation, quick internal tools, early pilots, and workflow discovery.
The mistake is assuming that “great for learning” automatically means “safe to own.”
Why Healthcare Is Different: “Compliance” Isn’t a Toggle
In most industries, “secure enough” can be a reasonable stepping stone. In healthcare, it’s a liability. Not because regulators hate innovation, but because compliance is evidence-based: you’re expected to prove you control access, track activity, and manage risk — not merely claim the platform is “HIPAA-ready.”

Take auditability. HIPAA’s Security Rule doesn’t ask whether your vendor has a nice security page — it expects you to implement mechanisms that record and examine activity in systems that contain or use ePHI (that’s the actual audit-controls standard). If your platform can’t give you the right logs, in the right granularity, with the ability to review them and respond, you don’t have “compliance.” You have a blind spot with a subscription fee.
And enforcement isn’t theoretical. OCR’s settlement with Memorial Healthcare Systems explicitly underscored the importance of audit controls, pairing a $5.5M payment with a corrective action plan.
The point isn’t “be afraid.” It’s: this is what “show me” looks like when something goes wrong.
Same with cloud and third parties: if a service maintains ePHI, you can’t wave your hands and skip the BAA step — OCR’s own guidance is blunt about that.
So yes, move fast. Just don’t confuse “fast setup” with “owned control.”
The 5 Ownership Gaps That Turn Into a Rewrite
By 2026, Gartner expects developers outside formal IT to make up at least 80% of the low-code tool user base. That’s great for speed — and a little terrifying without governance.
Here are the five gaps I see most often — the ones that turn “fast” into “we should rebuild this properly.”
1) Data Control
In healthcare, “data” isn’t just what powers the workflow. It’s retention and deletion rules, backup behavior, access history, and the ability to prove—on demand—what happened to PHI: where it went, who touched it, and what changed.
One compliance gotcha teams miss: even if a cloud provider stores only encrypted ePHI and can’t decrypt it (“no-view”), HHS can still treat them as a HIPAA business associate. Encryption reduces exposure; it doesn’t erase obligations.
And if “audit logs” means “trust our dashboard,” you don’t control PHI—you rent it.
This is where many no/low-code builds quietly fail: the “export” story covers rows and files, but not governance.
2) Access Control
Healthcare apps don’t have “users.” They have roles with consequences — plus exceptions that start as “temporary” and end up fossilized in production.
Access control becomes real the moment you need:
- least privilege
- clean deprovisioning
- separation between tenants/organizations
- support access without overexposure
- time-bound emergency override
- a defensible answer to “who could see what, when?”
This is also where “citizen-built” speed can backfire: permission drift is easy to create and hard to unwind if your model is configuration-first without strong guardrails. And once PHI is involved, “we think the roles are set up right” stops being an acceptable operating posture.
3) Integration Reality
This is the most predictable trap because it sounds so reasonable.
You launch the workflow first. Integrations become “Phase 2.” Then Phase 2 becomes the rest of your life.
Healthcare integrations aren’t just connectors. They’re reliability patterns:
- durable queues
- idempotency (so retries don’t double-book or duplicate)
- reconciliation
- monitoring
- failure modes that don’t silently drop clinical operations
No-code can be fine for proving integration shape early — but if the platform can’t support real integration mechanics, you end up building a second product made of glue.
4) Change Control
Prototypes change fast. Products change safely.
That means: versioning, review, traceability, rollback, and a release process that doesn’t feel like defusing a bomb on a Tuesday. No-code makes changes easy — which is the point — but it can also make production drift invisible: lots of edits, few guardrails, and a growing gap between “what we intended” and “what’s actually running.”
You feel it when teams start hesitating to touch production because they’ve been burned before. Or worse: they keep shipping because it’s easy, and later nobody can explain what changed, when, and why.
5) Observability & Incident Response
This is where the platform gets tested under stress.
When there’s an incident — security, availability, suspicious access, operational failure — you need answers. Not screenshots. Not “our vendor is looking into it.” Answers: what was accessed, what changed, by whom, and what systems were involved.
A concrete example: Green Ridge Behavioral Health reported a breach, OCR investigated, and the HHS resolution agreement describes a ransomware attack that resulted in the acquisition of PHI for over 14,000 patients. The settlement included a $40,000 payment and a Corrective Action Plan.
The “so what” for builders is simple: ransomware and incidents aren’t edge cases anymore. If your platform can’t give you the depth of logging and operational visibility you need to investigate, contain, and prove what happened, you don’t just lack observability — you lack defensibility.
The Hidden Bill: “Migration Tax” and Vendor Lock-In by Design
No-code usually sells itself as CapEx savings: ship now, worry later. The problem is that “later” has a price tag — and it tends to show up right when you finally have traction (the worst possible timing).
Most lock-in isn’t contractual. It’s technical. A lot of no-code platforms don’t give you a portable codebase you can host elsewhere — they store your app logic as metadata that only their runtime can interpret. So if pricing changes, a feature gets deprecated, or you outgrow the platform’s limits, “switching” isn’t a migration. It’s a rebuild.
And no, exporting a CSV doesn’t save you. You can often export rows, but not the structure:
- relational shape
- permissions logic
- workflow triggers
- version history
- the little operational duct tape that makes the system behave in production
Some platforms promise “code export,” but what you get can be so coupled to proprietary libraries that it’s effectively unmaintainable — which is just lock-in wearing a trench coat.
That’s the migration tax: the bill you pay for speed you already spent.
What “Full Code Ownership” Should Mean
“Full code ownership” isn’t a slogan. It’s a set of practical rights you either have on day one — or you’ll try to buy back later at rewrite prices.
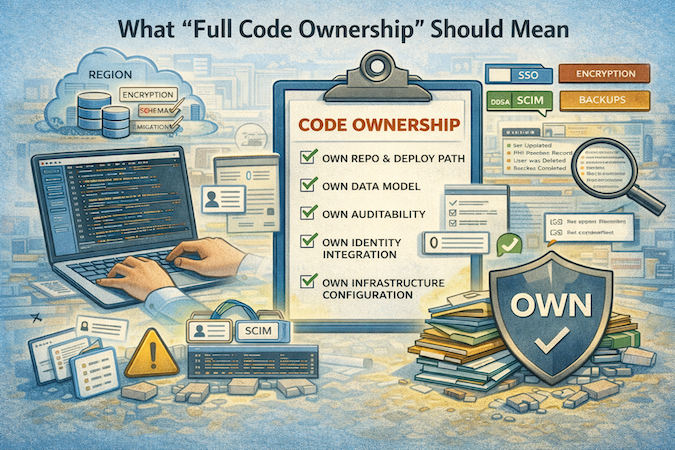
Here’s the definition I use:
- You own the repo and the deploy path. If the vendor vanished next week, you could still run the product (maybe with pain, but without panic).
- You own the data model. Schemas, migrations, constraints, and the ability to evolve the database without begging the platform for a new “field type.”
- You own auditability: logs are exportable, queryable, and retained to match your policies.
- You own identity integration. SSO/SCIM isn’t “enterprise fluff.” It’s how termination propagates and access doesn’t linger.
- You own infrastructure configuration (or at least transparent evidence). Region, backups, encryption posture, incident hooks, monitoring — in writing, not vibes.
And the big one: your IP lives in code you control, not inside someone else’s runtime as “configuration.”
A Practical Middle Path: Use No-Code, But Don’t Marry It
I’m not here to tell you to “never touch no-code.” That would be like telling clinicians to stop using templates because free text is more “pure.” The right move is to separate speed from dependency.
Use builder-style tooling to move fast on what benefits most from iteration: workflows, screens, role journeys, the boring-but-critical operational logic. That’s where no-code shines — fewer meetings, faster learning, less wasted build.
But draw a hard line around what must stay yours: the parts that define your product and your risk profile. Your core data model. Your permissions logic. Your audit trail. The integration layer that has to behave the same way every time, even when upstream systems misbehave. The deployment path that keeps you in control.
A good rule of thumb: use no-code to accelerate construction, not to surrender ownership.
Design your exit even if you never take it:
- Keep canonical data in structures you control.
- Make sure your app can be deployed and maintained without being trapped inside a vendor runtime.
- Treat platform conveniences as accelerators, not as the place your product’s DNA lives.
That’s how you ship faster and stay on your terms.
Decision Checklist: Questions to Ask Before You Put PHI In Anything
Before PHI touches a platform, I like to run a simple test: can you defend your choices in writing, with evidence, on a bad day? Because OCR settlements aren’t just for “big hospitals”—Raleigh Orthopaedic paid $750,000 over PHI shared without a BAA, and CCDH paid $31,000 because they couldn’t produce a signed BAA with a vendor.
Here’s the adult-supervision checklist (one line per question):
- BAA: Will the vendor sign a BAA before any PHI is stored, processed, or accessed?
- Subprocessors: Who are the subprocessors, and do you get notified when that list changes?
- “No-view” myth: If the vendor says “we only store encrypted data,” do they still acknowledge they’re a business associate? (They should.)
- Risk analysis: Can you point to your own risk analysis—not the vendor’s marketing page? (OCR has dinged orgs for “never conducted” a risk analysis.)
- Audit logs: Do you get detailed, exportable audit logs (who/what/when), and can you retain them to your policy?
- Access control: Can you enforce least privilege, and prove it with role definitions + audit history?
- Deprovisioning: Does SSO/SCIM exist so terminations propagate automatically (no “zombie access”)?
- Export formats: Can you export data + metadata (schemas, permissions model, audit history), not just CSV rows?
- Deletion guarantees: Can the vendor prove deletion across backups/replicas within a defined SLA?
- Regional hosting: Can you pin data residency and document it (especially if you sell into the EU)?
- Pen test evidence: Do you get recent security testing evidence (and a real vuln management process)?
- Incident process: What’s the incident notification timeline, and do you get forensic artifacts if needed?
- API realities: If your product ever needs to support access/exchange of EHI, do you have API control that won’t bottleneck you? (ONC’s Cures Act Final Rule is explicitly about supporting access/exchange of EHI and implementing information blocking provisions.)
Where Specode Fits: No-Code Speed, Full-Code Ownership
If you like the speed of builder-style development but refuse to gamble your product on vendor lock-in, that’s where Specode fits.

Specode is built around a simple promise: you can ship healthcare apps faster without surrendering ownership.
You don’t just “export something” — you get fully editable code your developers can work with directly, with no hidden calls to some secret platform SDK that only we can maintain.
Your team can take it over, extend it, and run with it; and if you want help with advanced workflows, integrations, or compliance hardening, our team can jump in too.
In other words: move fast now, keep your options later — on your terms.
Frequently asked questions
Yes — for workflow discovery, pilots, and internal tools where you’re learning fast and the stakes are controlled. The risk starts when a prototype becomes a product and you’re expected to prove control (auditability, access, incident response) instead of just claiming “HIPAA-ready.”
It’s not that no-code can’t ship workflows — it’s that the most important parts of the system can end up living somewhere you don’t truly control. When PHI is involved, the first serious audit, integration, or incident turns “fast setup” into “fragility with a subscription fee.”
The blog calls out five repeat offenders: data control, access control, integration reality, change control, and observability/incident response. If any of those are “trust our dashboard” instead of “export, query, retain, prove,” you’re likely paying the rebuild bill later — with interest.
Not reliably. Exporting rows (CSV) is not the same as exporting what makes the system work: schema shape, permissions logic, workflow triggers, version history, and operational glue. That gap is the “migration tax” — you don’t avoid the rewrite, you just delay it until you have traction (the worst timing).
At minimum: you own the repo and deploy path, the data model, and auditability (exportable/queryable logs retained to policy), plus identity integration and transparent infrastructure evidence. The “adult supervision” test is simple: could you defend the platform choice in writing — with proof — before PHI touches it?









