The Leanest Stack to Build Compliant Healthcare Apps
Here’s the problem with most “fast” launches: they’re fast until month three. Lean healthcare app development isn’t about cutting corners; it’s about cutting rework. The real enemies are compliance drift, brittle integrations, and stacks that look clever in a demo but collapse under audits.
In this guide, we map the terrain that actually matters: EHR connections that aren’t “just an API call,” payment flows that carry PHI, architecture choices that survive subpoenas, and a practical path to assemble HIPAA-ready modules without surrendering code ownership.
If you’re deciding between no-code sprints, custom marathons, or something saner in between, this is your field manual for building the smallest thing that responsibly works—and scales.
Key takeaways:
- Start monolithic, extract only proven bottlenecks; make the API gateway your compliance edge; treat serverless as a scalpel, not a hammer.
- Integrations kill “lean”: EHR writes need state machines, healthcare payments behave nothing like e-commerce, wearables explode time-series storage—operate through one policy edge with secure messaging and clean data storage.
- Specode = HIPAA-ready components + full code ownership: faster than no-code, more flexible than low-code, with AI-assisted assembly arriving to accelerate clinician-founder builds.
The $500K Mistake Hidden in Your "Lean" Healthcare Stack
You know that sinking feeling when you realize your "MVP" is actually an "MV - Please - rebuild - everything"? A developer on Reddit shared what happens when platform limitations meet real-world requirements. They'd built an app on Bubble that caught fire with corporate clients through a consulting agency.
European interest rolled in, they checked hosting options—$4,000/month for a dedicated instance. As a result, they had to rebuild the entire thing custom. Now imagine if they'd also needed HIPAA compliance, which Bubble doesn't even offer.
“You can’t outsource security. We have to ensure cloud providers adhere to the policies and regulations our industry requires—some solutions will be off the table.” — Bill Russell, former 16-hospital health-system CIO.
That's the $500K mistake hiding in plain sight: the hours burned migrating data, the months of parallel systems, the lost deals while rebuilding, and the team morale hit from doing everything twice. The healthcare app tech stack you choose on day one determines whether you're building an asset or accumulating debt.
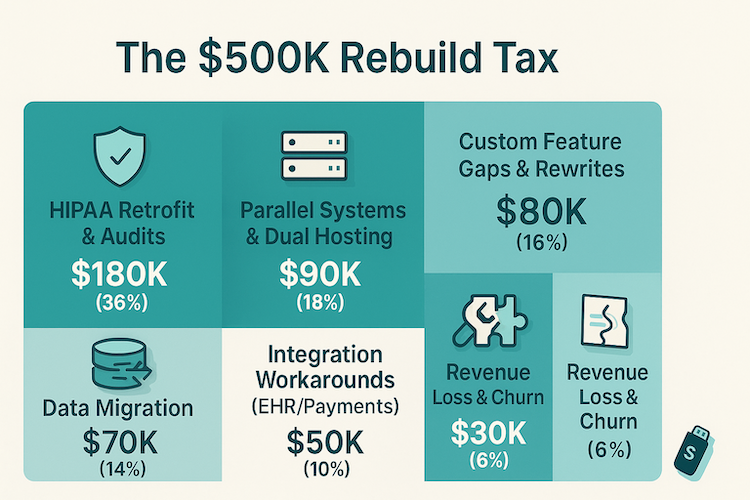
Here's what happens when you optimize for launch speed over operational reality.
The Compliance Wall (Month 3-6)
Your no-code platform doesn't offer BAAs. Your serverless functions can't guarantee PHI isolation. Your auth system lacks audit trails. Suddenly you're either lying to customers about compliance requirements or building workarounds that defeat the purpose of going lean.
One startup we tracked spent $180K retrofitting HIPAA compliance into their "simple" stack—more than building it right would have cost initially.
Reality check: HIPAA civil penalties can run $50k per violation, capped at up to $1.5M per year per violation category.
The Customization Wall (Month 6-12)
That drag-and-drop builder was perfect for your first 10 workflows. But workflow #11 needs custom clinical logic. Your healthcare regulations require specific consent flows. Your providers want their own dashboard views. Now you're fighting the platform instead of building features, writing JavaScript gymnastics to make square pegs fit round holes.
The Integration Wall (Month 12+)
EHR connections? "Not supported." Real-time eligibility checks? "Try our webhook workaround." Prescription routing? "Here's a forum post from 2019." The leanest stack healthcare app vision crumbles when you realize every integration requires duct tape and prayer.
The lesson? Scalability in healthcare isn't about handling traffic spikes. It's about handling compliance audits, payer integrations, and clinical workflows without your entire architecture becoming a liability. Choose your stack like you're planning to succeed, not like you're planning to pivot.
The Stack Spectrum: Mapping Your Options from No-Code to Full Custom
When evaluating a minimal tech stack healthcare app, you're facing a fundamental choice: how much control do you want versus how fast you need to ship? The market has fragmented into distinct camps, each with its own religion about the "right" way to build HIPAA compliant tech stack solutions. The truth is messier—and more interesting.
No-Code Platforms: The $100/Month Mirage
No-code sounds perfect until you hit the walls. Yes, platforms like Knack, Caspio, and AppSheet can sign BAAs and offer the basics—encrypted storage, audit logs, role-based permissions. They work brilliantly for simple workflows: patient intake forms, basic scheduling, wellness tracking. B2C wellness apps that don't touch complex clinical data can thrive here.
But here's what the marketing won't tell you:
- The compliance gap: Only 30% of no-code healthcare apps implement proper authorization for sensitive resources, according to recent security audits
- The feature ceiling: Need custom clinical workflows? Complex eligibility logic? Multi-provider coordination? You'll hit platform limitations fast
- The hidden rebuild: The need to rebuild everything on a "real" backend when a no-code MVP can't scale
The verdict: No-code works when your needs are genuinely simple. The moment you need provider-specific workflows, insurance eligibility checks, or API integration with clinical systems, you've outgrown the sandbox.
Low-Code Solutions: Enterprise Honey Traps
Low-code platforms promise the best of both worlds—rapid development with room to customize. OutSystems, Mendix, Microsoft Power Apps—they're sophisticated, feature-rich, and absolutely riddled with lock-in mechanisms that would make a 1990s software vendor blush.
The lock-in playbook is predictable:
- Proprietary data formats that make migration a six-figure project
- Platform-specific APIs that your entire app depends on
- "Open" architectures with closed-source dependencies
- Escalating costs once you're too invested to leave
Healthcare organizations report spending 70% more than initial estimates when factoring in hidden integration costs, training, and the inevitable vendor-mandated upgrades. Plus, in regulated industries like healthcare, you're not just locked into the platform—you're locked into their compliance posture, their security model, their audit trail implementation.
Traditional Development: The Expensive Insurance Policy
Custom development from scratch still dominates enterprise healthcare for one reason: control. When you're looking at $100,000 to $500,000 for a healthcare app and 12 to 40 weeks of development time, you're buying more than code—you're buying ownership of every decision.
The economics make sense in specific scenarios:
- Highly specialized clinical workflows that no platform supports
- Organizations with deep pockets and long horizons
- Teams that need to own every line of code for regulatory reasons
But let's be honest about what you're signing up for. 45% of software and app development projects are over budget while delivering 56% less value. Your initial quote is fiction.
The real costs emerge in month four when you discover your third-party integrations need custom adapters, your compliance requirements need specialized expertise, and your timeline has stretched because every feature is being built from zero.
AI-Assisted Builders: The Emerging Middle Ground
The newest entrants are rewriting the rules. AI-powered development platforms can now interpret healthcare requirements, generate HIPAA-compliant scaffolding in minutes, and automate 60% of the standard code patterns.
For example, Corti provides healthcare-native APIs that handle clinical workflows out of the box. These aren't drag-and-drop toys—they're sophisticated code generation systems that understand healthcare's unique requirements.
The AI-assisted approach brings genuine advantages:
- Faster iteration cycles: Generate, test, refine in hours instead of weeks
- Healthcare-aware development: Models trained on medical workflows understand HIPAA requirements
- Reduced boilerplate: AI handles the repetitive plumbing, developers focus on unique logic
But we're still in early days. AI-generated code needs human review, especially for compliance-critical paths. The tools excel at standard patterns but struggle with edge cases—exactly where healthcare apps tend to break. Ping us to hear how Specode’s AI builder handles edge cases.
Quick Decision Matrix
Your optimal path depends on three variables: complexity, growth trajectory, and regulatory burden.
Choose no-code when:
- Simple B2C wellness or fitness tracking
- No PHI or minimal compliance requirements
- Budget under $20K, timeline under 4 weeks
- Willing to rebuild if you outgrow the platform
Choose low-code when:
- Enterprise environment already invested in the platform
- Standardized workflows with minimal customization
- IT team comfortable with vendor dependency
- Budget includes ongoing platform fees
Choose traditional custom when:
- Unique clinical workflows no platform supports
- Absolute code ownership is non-negotiable
- Budget exceeds $200K with 6+ month runway
- In-house development team already in place
Choose AI-assisted assembly when:
- Need production-ready in weeks, not quarters
- Want code ownership without starting from scratch
- Budget in the $40K-$120K range
- Focused on proven patterns with some customization
The smart money is moving toward hybrid approaches—using cloud infrastructure that's proven, containerization for portability, and DevOps practices that keep you platform-agnostic.
Whether you choose Specode's component assembly model or another path, the key is maintaining optionality. Because the only thing certain about healthcare technology is that your requirements will change faster than your platform vendor's roadmap.
The Non-Negotiable Core: What Every Compliant Healthcare Stack Actually Needs
When you set out to build compliant healthcare app infrastructure, the phrase "minimum viable" takes on a whole new meaning. What passes for lean in consumer SaaS becomes a liability lawsuit in healthcare.

The bare minimum that actually survives a HIPAA audit? It's about 3x more complex than most founders budget for—and cutting corners here doesn't save money, it just defers the invoice to a moment you can't afford it.
Let's map the non-negotiables. Not the nice-to-haves or the "we'll add it later" features, but the foundational elements that keep you out of regulatory crosshairs and data breach headlines.
Authentication & Authorization: Beyond Username/Password
Basic login died in 2015. For HIPAA compliance, you need:
- Multi-factor authentication (MFA) for any admin or clinical user—not optional, not "coming soon"
- Role-based access control (RBAC) with granular permissions: e.g., a nurse shouldn't see billing data, billing shouldn't see clinical notes
- Session management with automatic timeouts (15-30 minutes of inactivity max)
- Password complexity requirements that actually get enforced, plus regular rotation policies
The authorization piece is where lean healthcare development often stumbles. It's not enough to know who someone is—you need to control what they can access, when they can access it, and maintain proof of every decision.
Audit Logs That Actually Work
Here's what separates compliant audit logs from the checkbox version:
Immutability is mandatory. Your audit logs need cryptographic timestamps and hash chains—if someone can edit the logs after the fact, they're worthless for compliance. Store them separately from your main database, ideally in a write-once storage system.
Completeness over convenience. Log every access attempt (successful or not), every data view, every export, every permission change. Yes, this means your audit log database will be larger than your actual application database. That's normal.
Searchability for investigations. When (not if) you need to respond to a breach investigation or compliance audit, you have 72 hours. Can you query "show me everyone who accessed Patient X's records between these dates"? If that query takes more than 60 seconds, your architecture is wrong.
Data Encryption: Both Layers Matter
"We use HTTPS" isn't data encryption—it's table stakes. For patient privacy protection:
- In transit: TLS 1.2 minimum (really should be 1.3 in 2025), with certificate pinning for mobile apps
- At rest: AES-256 for databases, file storage, and backups—including dev/staging environments
- Key management: Separate key storage from data storage, with automated rotation every 90 days
The encryption gap that kills most "lean" stacks? Backups and logs. That database dump sitting in S3? Encrypted. The debug logs your monitoring service collects? Better not contain PHI, or they need encryption too.
Disaster Recovery Isn't Optional
HIPAA requires you to maintain data availability. Your disaster recovery plan needs:
- Automated backups every 24 hours minimum
- Geographically distributed backup storage
- Tested restoration procedures (actually tested, not theoretical)
- Maximum 72-hour recovery time objective (RTO)
Skip this, and your first ransomware attack becomes your last day in business.
The Build Approach Breakdown: Real Costs and Timelines
The real cost of building a healthcare app isn't on the pricing page—it's buried in rebuild cycles, compliance audits, and the three platform migrations nobody warned you about. After watching teams blow through budgets trying to scale a no-code MVP or watching "custom" builds take 14 months to ship basic features, here's what the actual math looks like across different approaches.
No-Code Platforms: The $70K Ceiling Problem
No-code healthcare platforms promise you'll ship in weeks, and they're right—until you're not. Basic apps run $30,000 to $120,000, but that's where the happy path ends. The moment you need custom PHI handling, complex eligibility logic, or integration beyond their pre-built connectors, you hit the platform ceiling hard.
What vendors don't advertise: that "quick win" becomes technical debt when you need to:
- Handle dual insurance workflows (primary/secondary coordination)
- Implement provider-specific consent flows
- Build custom audit trails for state-specific requirements
- Scale beyond 10,000 active users without performance degradation
The rebuild cost when you outgrow the platform? Usually matches or exceeds your original investment.
Low-Code Healthcare Platforms: The Hidden Subscription Trap
Low-code platforms targeting healthcare start around $90 per user per month for standard licensing, but that's before you've written a line of code. Enterprise healthcare features push annual platform costs well past $100K before factoring in:
- HIPAA-compliant hosting upgrades
- Additional environments for staging/testing
- Per-provider or per-API call pricing
- Premium support (mandatory for healthcare)
The real catch: you're still coding 30-40% of the application, just with proprietary abstractions. One mental health platform discovered their "low-code" solution required 400+ hours of custom scripting for lean healthcare app development needs—at which point they'd have been better off with full control.
Component-Based Assembly: The 80/20 Reality
Here's where the economics shift. Start with pre-built, HIPAA-ready components for the undifferentiated 80%: authentication, RBAC, consent management, audit logging, secure messaging, scheduling. Then invest your engineering effort in the 20% that makes your solution unique.
This minimal healthcare architecture approach typically lands at:
- Initial assembly: Under $2K-$4K for core platform setup (Specode without customization)
- Custom integration: $30K-$60K for your specific workflows
- Timeline: 4-8 weeks to pilot-ready vs 12-18 months for traditional comprehensive platforms
The key differentiator: you own the code (NB not with all solutions, but 100% with Specode). No rebuild cycles, no vendor roadmap dependencies. When that edge-case state regulation drops or your biggest customer needs custom reporting, you adapt without negotiating with a platform vendor.
Full Custom Development: When "Expensive" Becomes Economical
Full custom healthcare apps run $70,000 to $500,000, with most landing in the $150K-$450K range for production-ready systems. Sounds expensive until you run the five-year TCO against platform alternatives:
*Includes platform fees, likely rebuild costs, and workaround development
Custom becomes the "lean" choice when you have:
- Complex clinical workflows requiring deep EHR integration
- Multi-state operations with varying compliance requirements
- High-volume usage (100K+ monthly active users)
- Novel care delivery models that don't fit platform templates
The Compliance Tax Nobody Budgets For
Here's what makes healthcare different: implementing privacy and security measures adds at least $20,000 to total costs, but that's just the entry fee. The real compliance costs compound through:
Development phase (adds 20-30% to base cost):
- PHI protection architecture design
- Encryption implementation (transit/rest)
- Audit logging infrastructure
- Consent management systems
- Break-glass access protocols
Pre-launch certification (adds 10-15%):
- HIPAA risk assessment ($5K-$15K)
- Penetration testing ($10K-$25K)
- SOC 2 Type I audit ($20K-$30K)
- State-specific compliance reviews
Ongoing maintenance (adds $2K-$10K/month):
- Quarterly security updates
- Annual audits and recertification
- Monitoring and incident response
- Compliance documentation updates
- BAA management with all vendors
The Speed-to-Market Reality Check
The four-month savings between approaches isn't linear—it's logarithmic in impact. Traditional HIPAA-compliant development takes 3 to 18 months, while component-based assembly with proven building blocks can deliver pilot-ready systems in 4-8 weeks.
But here's what those months mean in practice:
- Competitive advantage: First-mover in your specialty or region
- Revenue acceleration: 3-4 months of additional revenue generation
- Iteration cycles: 2-3 rounds of real user feedback before competitors launch
- Payer contracts: Meeting open enrollment deadlines vs. waiting another year
Making the Build vs. Buy Decision
Stop asking "how much does it cost?" and start asking "what's the cost of being wrong?" If you're testing a new care model with 50 patients, burn the no-code runway. If you're building the operating system for your practice's next decade, invest in ownership and flexibility.
The sweet spot for cost-effective healthcare app development usually lives in the middle: proven components for commodity features, custom code for competitive differentiation, and continuous iteration based on actual usage—not platform constraints.
For teams ready to move past the build-vs-buy debate, the question becomes: how quickly can you assemble proven healthcare components into something uniquely yours? That's where platforms enabling component-based assembly change the entire economic equation.
Architecture Patterns That Scale Without Breaking Compliance
The healthcare industry's relationship with microservices is complicated. While 89% of technology leaders agree that companies not effectively supporting microservices will be less able to compete, healthcare's reality is messier.

Your PHI flowing through distributed services creates audit nightmares, your incident response gets 10x harder when a breach spans 50 microservices, and suddenly your "simple" patient portal needs a service mesh just to handle basic authentication.
Let's cut through the architecture religion and talk about what actually works when HIPAA auditors come knocking.
The Monolith Isn't Dead (It Just Got a Bad Publicist)
For a 5-provider clinic handling 200 patients daily, a well-architected monolith beats microservices every time. You get:
- Single audit trail: One application, one database, one place to prove who accessed what
- Simpler BAA management: Fewer vendors to sign agreements with
- Lower operational overhead: One deployment CI/CD pipeline, one monitoring stack, one team to train
- Faster incident response: When something breaks, you know exactly where to look
The healthcare microservices market is projected to grow from USD 390.32 million in 2024 to USD 1,751.26 million by 2032, but that doesn't mean every practice needs to jump on board. If your monolith handles your transaction volume, maintains sub-second response times, and passes compliance audits—keep it. The best architecture is the one that ships features without breaking compliance.
When Microservices Make Sense (And When They Don't)
Large health systems and platforms need microservices for legitimate reasons. When you're processing millions of claims, handling telehealth sessions across time zones, or integrating with 15 different EHR systems, the modularity pays off.
The sweet spot for healthcare microservices:
- Independent scaling for high-traffic services (appointment booking, lab results)
- Isolation of third-party integrations (each pharmacy API in its own service)
- Multi-tenant platforms serving different compliance requirements
- Teams larger than 50 developers who need parallel deployment paths
Where microservices create more problems than they solve:
- Small practices with under 1,000 daily transactions
- MVP applications still finding product-market fit
- Teams without dedicated DevOps resources
- Systems where data consistency matters more than scaling flexibility
The API Gateway: Your Compliance Command Center
Here's what most architects miss: your API gateway isn't just traffic management—it's your HIPAA compliance enforcement point. A well-designed API gateway acts as a vital intermediary managing, securing, and optimizing communication between countless microservices while meeting strict HIPAA compliance standards.
Non-negotiable gateway features for healthcare:
- Centralized audit logging that captures every PHI access attempt
- Token validation with automatic expiration for abandoned sessions
- Rate limiting by user role (providers get higher limits than patients)
- Automatic PHI scrubbing from error messages and logs
- Request/response encryption independent of backend services
Whether you choose AWS API Gateway, Azure API Management, or open-source solutions like Kong, the pattern remains: funnel everything through a single, auditable entry point. Your gateway becomes the one place where compliance, security, and operational visibility converge.
Serverless: Great Until It Isn't
Serverless promises the dream: infinite scale, zero infrastructure management, pay-per-use pricing. For healthcare, the reality is more nuanced.
Where serverless shines:
- Batch processing of lab results or claims (Lambda + S3)
- Image resizing for telehealth platforms
- Webhook handlers for EHR notifications
- Document generation for patient summaries
Where serverless becomes a compliance nightmare:
- Long-running PHI processing (15-minute Lambda timeout hits mid-operation)
- Complex multi-step workflows requiring state management
- High-frequency, low-latency requirements (cold starts kill patient experience)
- Debugging production issues across 200 Lambda functions
All AWS services including Lambda are HIPAA-eligible, enabling you to store, process, and transmit PHI, as long as it complies with the BAA. But HIPAA-eligible doesn't mean HIPAA-optimized. Your serverless functions need explicit VPC configurations, careful IAM role management, and comprehensive CloudTrail logging—complexity that often negates the "serverless simplicity" pitch.
The architecture pattern that actually scales without breaking compliance? Start monolithic, extract services when you have concrete scaling bottlenecks, use your API gateway as a compliance chokepoint, and treat serverless as a specialized tool rather than a default choice. Healthcare isn't Netflix—your architecture should optimize for audit trails and data integrity before infinite scale.
The Integration Reality Check: What Kills Lean Stacks
Every “it’s just an API” turns into four problems: identity, data model, workflow semantics, and who takes the blame when PHI leaks.

EHR Integration — Never a Single Call
Electronic health records expose dozens of surfaces—FHIR, HL7v2, vendor-specific REST—with different auth, patient-matching rules, and write constraints. Reading demographics is table stakes; creating encounters, pushing notes, or attaching imaging requires consent flows, idempotency, and downtime handling.
Sandboxes rarely mirror prod. Version drift is constant. Plan for retries, reconciliation queues, and a backstop when the EHR says “accepted” but the downstream team doesn’t see it.
Payment Processing in Healthcare Isn’t E-commerce
Cards, HSA/FSA, and payer splits collide with medical necessity and pre-auth. Line items carry PHI; put the wrong field in a webhook and you’ve just leaked diagnosis codes to a non-BAA’d vendor.
PCI scope is solvable; HIPAA scope is what bites. You’ll need
- eligibility checks
- intelligent write-offs
- refund flows that don’t desync with claims
Treat payment metadata like PHI unless you can prove otherwise.
The Wearables/Devices Trap
Great for demos, brutal in production. Tokens expire, Bluetooth flakes, and firmware updates change payloads. Time-series data storage explodes; you’ll need windowing, denoising, and retention rules that map to consent.
If the device output informs diagnosis, your workflow suddenly looks regulatory-adjacent. Encrypt everything, tag by patient, and assume gaps—never gate critical clinical logic on consumer hardware.
Here’s how to keep a lean tech stack HIPAA compliant without tripping over the real world.
Third-Party Services That Look Cheap—Until the BAA
The bargain queue, logger, SMS, video, or analytics tool often won’t sign a BAA, or only under enterprise pricing with strict subprocessor limits. Even when “HIPAA-eligible,” you own configuration: access scopes, log redaction, backups, and breach notifications. Chain of custody matters—one unsanctioned export to a support inbox is a reportable event.
Operate through the Right Edges
Push secure messaging, scheduling, and document exchange through a single policy edge (API gateway) with token scoping, immutable audit events, and response sanitization. Treat EHR writes as state machines, not RPCs. Separate PHI from operational logs. Assume retries, versioning, and fallbacks on day one.
How Specode Helps Build Truly Lean Healthcare Apps

You don’t need “magic.” You need assembly. Specode ships pre-built, HIPAA-compliant components—so your team focuses on last-mile logic instead of rebuilding plumbing. These cover the majority of common needs with security measures baked in.
- Auth & roles, audit logs, e-consent
- Secure messaging, scheduling, eligibility
- Payments, EHR, API connectors
AI Assistant: Build by Chat, See It Live
Describe what you want; watch it take shape. The assistant turns plain-English prompts into working features with an immediate preview—scaffolding screens, data models, and RBAC by default.
- Connect your own data early and it shapes the UI around your real entities, not mockups.
- Fully brandable, so your app looks like your product from day one.
Integrations without the drag. Flip on the services that matter—payments, telehealth, eRx, wearables, EHRs—and the assistant stitches them into your flows. Guardrails keep experiments safe (Change Log restore, role-scoped testing). No AI magic—sequence and ruthless focus.
Your team, our team, or both. Combine the AI builder with custom development by your engineers or ours. On the Custom tier, you can also spin up purpose-built AI agents and get hands-on help from Specode devs.
Own the Code, Skip the Lock-in
You get full code ownership and a clear escape hatch when you outgrow us—no proprietary ceiling, no rewrite tax.
Faster Than No-code, More Flexible Than Low-code
No-code is fast until healthcare constraints hit; bespoke custom is flexible until it burns months on basics. Our component assembly model splits the difference:
- Wire proven building blocks, customize where it matters
- Keep velocity without compromising auditability
- Standardize integration patterns across services
Proof in Market: AlgoRX
Using Specode components — eligibility, provider workflows, ePharma routing, multi-pharmacy checkout — AlgoRX hit $1M+ in sales by month two and reported 12× ROI, avoiding both the no-code trap and an all-custom rewrite.
What’s Next: AI-assisted Assembly
In the coming weeks, we’re rolling out AI helpers that let clinician-founders compose features even faster, while our team remains on call for the hard edges—EHR paths, payments, compliance choreography.
If you’re optimizing for outcomes, not theater, Specode is the shortest path to a HIPAA-ready MVP you can extend without drama. Assemble what’s standard, tailor what’s proprietary, and keep ownership from day one—the pragmatic way to build a healthcare app at a minimal cost without sacrificing integrity.
Start free on Specode—make one small move (“enable auth + e-consent”), preview, then stack the next (“add audit logs”), then connect a sandbox EHR for write-back. Three tiny steps = a lean, compliant core you can extend without rewrites.
Frequently asked questions
Shipping the smallest responsible product that passes audits, logs every PHI touch, and avoids rebuilds—speed without compliance debt.
Monolith for focus and clear audit trails; extract services only when a domain shows real scaling or isolation needs.
Yes, for bursty, stateless jobs—if VPC, IAM, logging, and redaction are nailed. Avoid for long-running or low-latency clinical paths.
Identity, consent, version drift, and PHI in payloads turn calls into workflows. Treat writes as state machines with retries and reconciliation.
Pre-built HIPAA components you own and can customize—no lock-in, audit-ready from day one, and faster assembly with upcoming AI helpers.









